Enter your email address to receive the latest ITVET news, market insights, and useful IT tips.
PDFs are widely used in business because of their convenience, cross-platform compatibility, and trusted appearance. Yet, this trust has made them a favourite weapon for cybercriminals.
Research by Check Point shows that around 22% of all malicious email attachments are PDFs. In other words, almost one in four phishing campaigns relies on this format. This means protecting your business from malicious PDFs is a critical part of any cyber security strategy.
In this guide, we’ll answer the key questions about malicious PDF files, explain how attackers exploit them, and share practical steps to keep your business safe.
How do malicious PDF files work?
Malicious PDF files exploit software vulnerabilities and human trust. While a PDF may look harmless, attackers can hide code, links, or attachments that trigger when the file is opened. These tactics often combine technical exploits with social engineering to bypass security tools and trick employees into taking action.
Common tactics used by attackers:
- Impersonation tactics: PDFs disguised as invoices, contracts, or compliance forms from trusted sources like banks, HMRC, or delivery companies.
- Embedded scripts: JavaScript or macros that run automatically in vulnerable PDF readers, downloading malware or exploiting weaknesses.
- Hidden attachments: Extra files, such as executables, that launch without the employee realising.
- Phishing links: Embedded links to fake login pages or malicious websites designed to steal credentials.
- Encrypted or password-protected files: PDFs encrypted to bypass email filters, with employees tricked into downloading a fake “decryption tool” that installs malware.
- Exploitation of software flaws: Unpatched or outdated PDF readers that allow attackers to execute malicious code directly.
- Social engineering hooks: Messages that create a sense of urgency or appear official, pressuring employees to open the PDF immediately.
This mix of technical and psychological methods makes malicious PDFs a persistent and effective threat. Understanding these methods helps businesses design layered defences that protect employees and systems from potential attacks.
How can my business prevent PDF attacks?
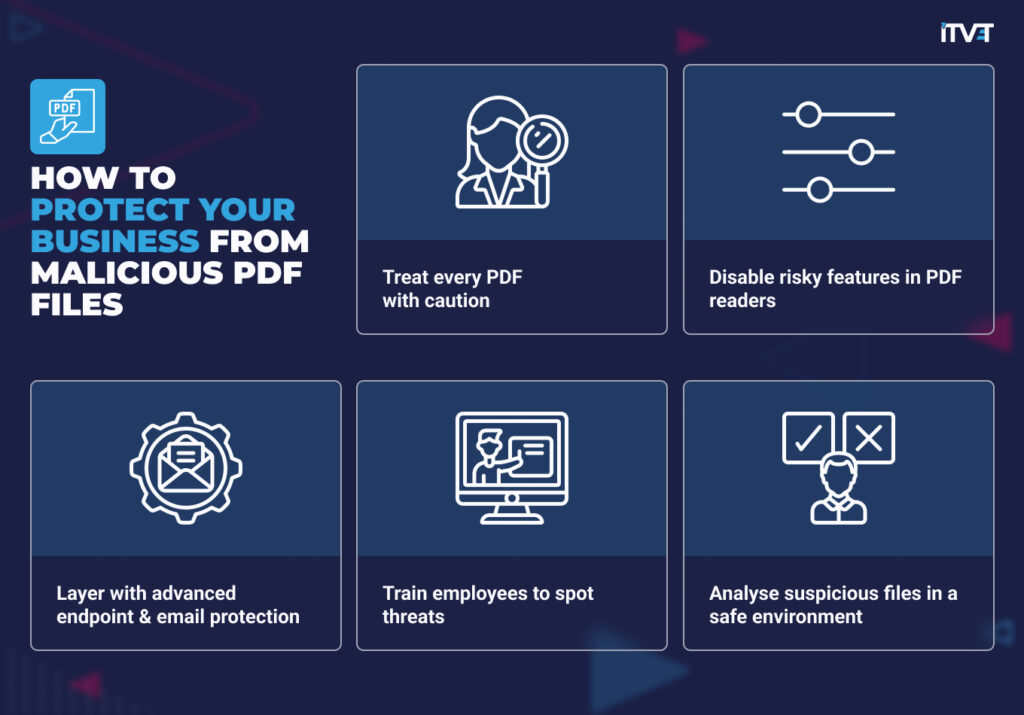
1. Treat every PDF with caution
- Avoid opening PDFs from unknown or unexpected sources.
- Double-check with the sender before opening sensitive files like invoices or contracts.
- Be suspicious of encrypted PDFs that require third-party tools to unlock.
2. Disable risky features in PDF readers
- Switch off JavaScript functionality in your PDF reader – it’s rarely needed for business use and is a common attack vector.
- Disable automatic launching of embedded files or multimedia to block hidden attachments.
- Keep your PDF readers regularly updated to fix vulnerabilities before attackers can exploit them.
3. Layer with advanced endpoint and email protection
- Deploy endpoint security solutions with next-gen antivirus and behavioural analysis to detect and block threats.
- Use cloud-based email filters that scan all attachments before delivery.
- Enable attachment sandboxing, so suspicious PDFs open in a safe, isolated environment first.
4. Train employees to spot threats
Human error is the weakest link in any cyber defence.
Training should include:
- Awareness of phishing campaigns using PDF attachments.
- Simulated exercises where employees must identify suspicious emails.
- Guidance on reporting unusual files confidently without fear of blame.
- Clear rules: never enable macros, run external tools, or click embedded links in PDFs.
5. Analyse suspicious files in a safe environment
If someone receives a suspicious PDF, they should immediately report it to their IT team.
The IT team’s next move should include:
- Use isolated virtual machines or sandbox environments to safely test the file.
- Apply tools like pdfid.py or pdf-parser.py to scan PDFs for hidden payloads.
- Keep detailed logs of attempted attacks to refine future training and security policies.
Why is proactive defence against malicious PDFs so important?
As businesses embrace digital transformation and remote working, cyber threats are escalating. Email has become the backbone of daily operations, and PDFs are a trusted part of that workflow. Cybercriminals exploit this dependency to deliver ransomware, steal sensitive data, and disrupt business operations.
Attackers favour PDFs because they can bypass traditional security tools and take advantage of human behaviour. A single malicious file can trigger data breaches, operational disruptions, regulatory fines, and loss of trust with clients and partners. The financial and reputational impact far outweighs the cost of investing in preventive measures.
Why isn’t traditional antivirus enough?
Traditional antivirus software can only block known threats. Modern attacks evolve rapidly, creating new variants that evade outdated definitions. Relying solely on traditional antivirus leaves businesses vulnerable to data breaches, operational disruption, and reputational damage. That’s why multi-layered cyber security is essential, providing robust protection even against the most sophisticated threats.
How ITVET helps businesses defend against malicious PDFs
At ITVET, cyber security isn’t just a service – it’s embedded in everything we do. As a Managed Services Provider (MSP), we integrate robust security measures into every solution, ensuring your business is protected at all levels. Our proactive approach combines expert knowledge with advanced technology to safeguard your operations from evolving threats.
ITVET helps businesses defend against malicious PDFs through:
- Advanced filtering: Advanced email security tools that neutralise harmful content before it reaches employees’ inboxes.
- Endpoint protection: Solutions that block malicious files at the device level, stopping threats before they cause harm.
- Employee empowerment: Tailored training and simulations to build confidence in spotting and handling suspicious files.
- Incident response: Suspicious files are investigated safely in controlled environments, minimising risk.
- Strategic guidance: Aligns your cyber security strategy with compliance requirements and business objectives, ensuring long-term protection.
Stay ahead of cyber threats with ITVET. Our cyber security-first approach ensures businesses don’t just react to malicious PDFs. We help you prevent attacks, respond quickly to incidents, and protect your operations, data, and reputation. Partner with us to stay secure and confident in a rapidly evolving threat landscape.
Take the next step
PDF threats are increasing, but your business doesn’t have to be at risk. Combining employee awareness with advanced security solutions can dramatically reduce the chance of a successful attack.
ITVET helps organisations across the UK build stronger, safer IT environments. Get in touch today to strengthen your defences and protect your business from malicious PDFs.






