Enter your email address to receive the latest ITVET news, market insights, and useful IT tips.
Phishing accounted for 84% of cyberattacks on businesses in 2024, costing the UK economy billions. Malicious emails containing harmful links are by far the most successful method used by criminals. It’s now estimated that over 49% of emails sent are spam. This number only accounts for those emails detected by various spam filters. It doesn’t include the high percentage of ‘allowed’ emails that clog up our mailboxes daily.
From fake invoices to email scams impersonating Amazon, PayPal and more, it’s hard to avoid. With these threats growing in volume and sophistication daily, it’s vital that businesses understand how to improve email security. In this blog post, we outline eight email security tips to help protect your business.

What is email security?
Email security is how you protect your business against malicious email-based threats and unwanted communications. A robust email security strategy uses a combination of tools and policies to ensure the availability, integrity and authenticity of your email communications.
Why is email security important?
Email security is important because it protects your business from cyberattacks. All it takes is one misguided click to cause a security crisis and threaten your business financially.
There’s no doubt that email remains the most popular, and quickest way to communicate in business. Over 333 billion emails are sent and received each day globally, giving cybercriminals ample opportunity to attack.
Malicious emails can compromise your network, systems and data and the consequences of this can be catastrophic. In 2023, The average cost of a data breach was $4.45 million.

Common types of email attacks
Phishing
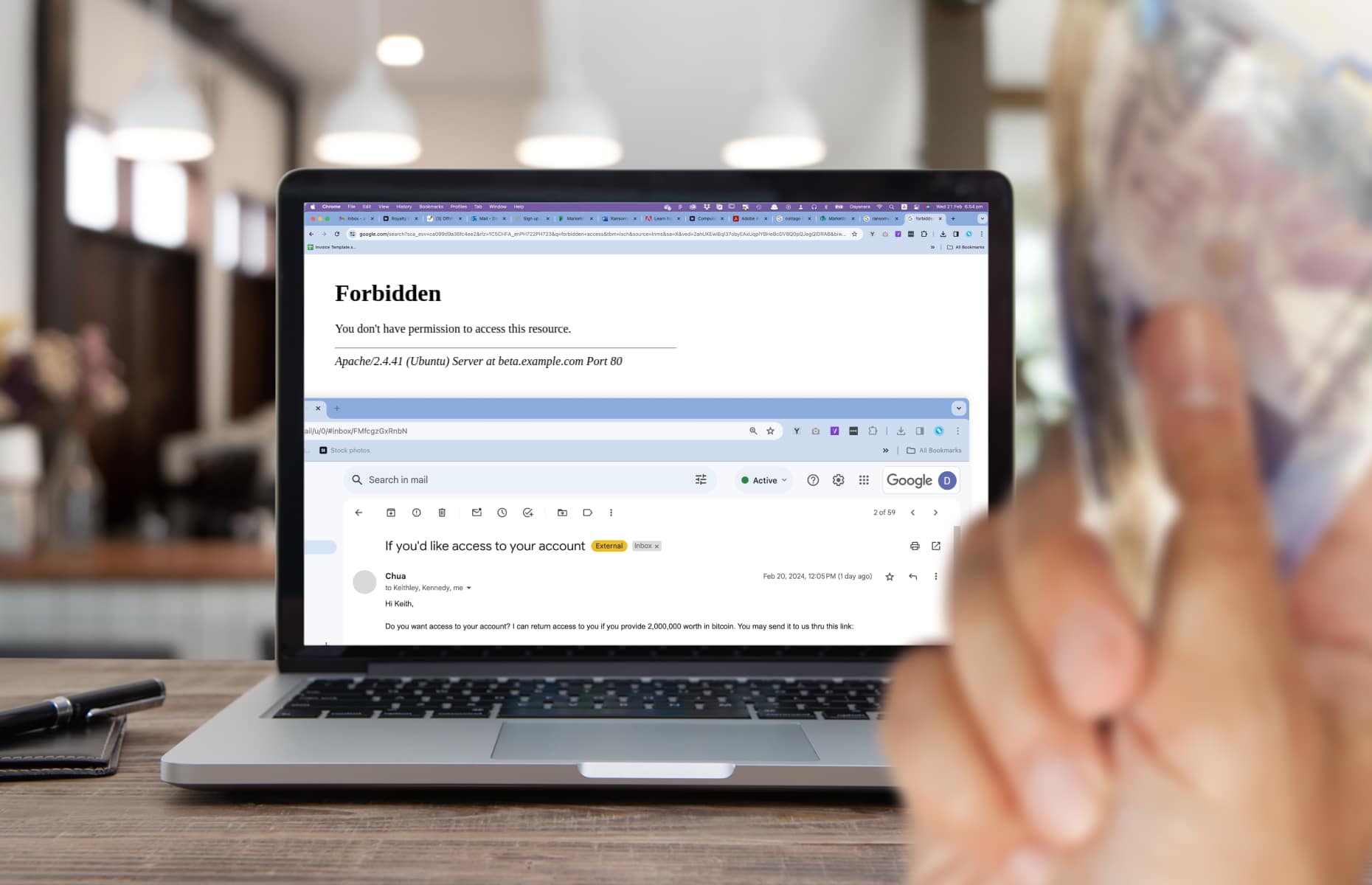
Phishing, a type of social engineering attack, steals your private information by using a fraudulent email disguised as a legitimate one. The email usually contains a bad link that directs you to a fake webpage where you’re asked to submit private information. Different types of phishing attacks include spear phishing, vishing and whaling.
Malware
Similar to phishing, a malware attack tries to trick you into doing something ‘wrong’. In this instance, downloading an infected attachment. This gives hackers the opportunity to damage, disrupt or gain unauthorised access to your computer system. Different types of malware attacks include viruses, worms, spyware and ransomware.
Business Email Compromise (BEC)
Business Email Compromise (BEC) is a type of email fraud that specifically targets employees, especially those in the finance team. The email uses a false identity, usually someone in senior management, and tricks them into transferring money to illegitimate accounts.
Account Takeover (ATO)
In an Account Takeover (ATO) attack, cybercriminals gain unauthorised access to your email account through phishing or credential theft. Once in control of the account, they can monitor messages, steal information, or use the account to launch further cyberattacks.
Spam
Spam refers to unsolicited, unwanted email messages sent in bulk. Businesses often use spam for marketing purposes. This isn’t malicious but it can be a nuisance and drain on resources. Scammers also use spam to send bad links and malicious attachments as part of a cyberattack.
How to improve email security
While the most up-to-date and stringent email security systems can take care of the majority of dangerous emails, it’s virtually impossible to eradicate them completely. There are various reasons for this. It’s nothing to do with the systems themselves, but it’s largely down to the way they’re configured, and the way emails are used by businesses.
Let’s take a quick look at some email security tips:
Company email setup
1. Do all employees need email?
This may seem obvious, but if employees only use email for internal purposes then turn off their external emails. It’s worth keeping in mind that as more and more companies adopt Microsoft Teams internal email usage is dropping significantly.
2. Limit emails to approved senders only
If users only send and receive emails to known contacts, then it’s possible to block all emails from unknown senders. This can even be put in place for generic or departmental email addresses such as ‘sales’ or ‘enquiry’.
If an email is sent from an unknown sender an autoresponder can be sent back, alerting them that it’s been blocked. This can include a link to the contact form on the company website.
An alert can also be sent to the recipient to notify them that an email has been blocked. A copy of the email should be available in the email filtering system just in case.
3. Restrict emails due to content
While it can be frustrating for employees to have genuine emails trapped in junk, it’s worth rethinking the type of content that’s allowed to be delivered to your business, even from your approved senders’ list.
For example, you could set up a rule to automatically quarantine all emails with attachments or links to shared documents. This means employees would have to release them from quarantine. Although this doesn’t completely rule out the threat, it does make the employees stop and think before they release a quarantined email. Appropriate warnings reminding them about the dangers of clicking links and downloading attachments can also be displayed when they’re releasing emails.
4. Employee training
It’s well known that employees are responsible for most data breaches by unknowingly clicking on phishing links or downloading harmful attachments. Employee training is probably the most important part of email security, yet sadly it’s rarely provided. Most companies rely solely on the email security systems and procedures they have in place, but clearly, this isn’t working.
We only have to look at the data to establish that threats are increasing at an alarming rate and are only set to get worse. Training your employees provides them with an understanding of why email security is important and the tools to prevent attacks. This may lessen the frustration when they need to release the odd genuine email from the spam filter.
5. Internet security
Most phishing and scam emails rely on an active internet connection to be able to initiate an attack or scam. Therefore, having a sophisticated internet security solution such as ‘Cisco Umbrella’ can be key. For instance, if an unsuspecting user clicks on a malicious link Cisco will flag the corresponding IP address as malicious to help avoid an attack.

Security your email with a dedicated security system
1. Initial setup and configuration
If you don’t already have a dedicated email security system, it is crucial to consider investing in one such as Trend Micro Hosted Email Security.
For those already employing one, ensuring its proper configuration and ongoing maintenance is key. Our experience has shown that many issues stem from inadequate setup and configuration, which are then subsequently ignored by IT teams. The process of establishing your email security system should not be seen as a one-time setup, but one that requires ongoing attention.
Businesses should explore the option of enlisting the services of an email security specialist. At ITVET, we can assist you in establishing a robust email security system and provide training for your in-house IT team.
2. Create a safe senders list
A crucial part of any email security system is building and maintaining an accurate list of known email addresses or domains that your company does business with. This is just as important as determining a bad senders list (blacklist).
Building a known good senders list helps prevent systems from frustratingly blocking potentially wanted emails as spam. However, it’s still possible to receive dangerous or virus-laden threats from known good email addresses if they have been compromised.
If your email security system is set up correctly it should automatically block any emails containing malicious attachments or links. Given the speed at which cyber threats evolve, even the most stringent system can allow the odd malicious email through. That’s where your company’s email setup and employee training come into play.
3. Establish security filtering levels
It can be tough to find the right balance between being too strict with email security and letting too much spam get through. It’s frustrating when real emails end up in the spam folder, but the email security system still needs to catch bad emails. That’s where having an email security expert can help. They can work with you to figure out the right settings.
After you set up the system, it might take a few weeks to get it just right and make any necessary changes. But it’s safer to occasionally block a real email than to let spam through.

Benefits of email security
- Protects against phishing
Phishing can cause catastrophic data breaches and compromise your computer system with malware. Email security can detect and resolve phishing attempts to keep your business secure and operational. - Safeguards your data
Email encryption can help protect your data including credit card numbers and bank account details, making it harder for cybercriminals to get their hands on them. - Prevents compromised accounts and identity theft
Email encryption can help prevent cybercriminals from stealing login credentials and other personal data or installing malware. This reduces the risk of your email accounts becoming compromised and falling victim to identity theft. - Detects and blocks malicious emails and spam
Email security software adds extra layers of security that can help detect and quarantine malicious emails and spam that get past the spam filter. - Ensures compliance
Email security can help businesses avoid costly data breaches and remain compliant with data protection regulations such as GDPR.
Summary
Email is an essential communications tool for businesses but it’s also the primary target for cybercriminals. Given the sheer volume and complexity of attacks, it’s important to know how to improve email security and make systems as secure as possible. Get in touch to find out more about our email security tips and how we can help.